Information Technology Resource Management (ITRM) Supporting Documents
PSG by Topic
Pursuant to Governor Youngkin’s Executive Order 30 (EO 30 PDF | news release), visit VITA's section to learn more about the Virginia standards on Artificial Intelligence use by state agencies.
Achieving the ultimate enterprise architecture (EA) requires collaboration, cooperation and coordination among agency business stakeholders, systems developers, partners and technology infrastructure providers. EA contributes to this collegial environment through EA policies (EA 200), EA standards (EA 225) and EA reports containing guidelines, recommendations and best practices which address all components of commonwealth EA. The policies, standards and reports provide requisite guidance and technical direction for the Commonwealth towards achieving an envisioned and evolving to be EA.
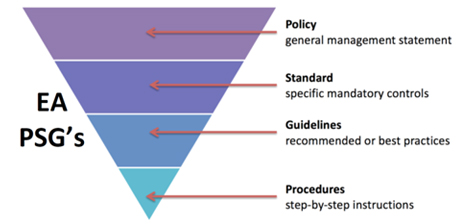
Executive branch agencies shall comply with the direction provided by the EA when developing and implementing technology solutions and the corresponding IT infrastructure required in supporting the business needs of the Commonwealth.
It is the intent of EA to standardize and simplify the many technologies and products in use throughout the commonwealth which generally results in a reduction in the number of technologies and products used to develop and support production systems. To support the intent of EA, we will continue ongoing development and implementation of EA and related standards.
Please refer to the following documents for guidance and direction:
- Enterprise Architecture Policy (EA200)
- Enterprise Architecture Standard (EA225)
- Cloud Based Hosting Services IT Solutions Policy (EA300) (02/26/2022)
- Enterprise Data Standards
Information Security Policies
Information Security Standards
- Information Security Standard (SEC530.01.1)
- IT Risk Management Standard (SEC520)
- IT Security Audit Standard (SEC502)
- Security Awareness Training Standard (SEC527)
- IT Standard Use of Non-Commonwealth Computing Devices to Telework (SEC511)
- Removal of Commonwealth Data from Electronic Media Standard (SEC514)
- Secure Remote Access to Online Court Documents Standard (SEC503-02.2)
- Virginia Real Property Electronic Recording Standard (SEC505)
- Data Classification Standard (SEC540)
Superseded Standards
Tools and Templates
- Agency Security Awareness Training Solution Form
- Agency Security Awareness Training Verification and Compliance Form
- Annual Risk Assessment Review and Certification
- Application Template
- Archer User Manual
- Audit Remediation Plan Template (also called Audit Corrective Action Plan (CAP))
- BIA Template
- COV ISO Certification and Continuing Education Requirements
- Data Set Template
- Data Removal
- COV Security Standard Exception Form
- Interoperability Security Agreement Template
- IT Risk Assessment Plan Template - Word
- IT Security Audit Plan Template - Word
- IT Security Audit Resources Template
- IT Security Policy & Procedure Templates
- SEC527 Crosswalk 2025
- Mission Essential Function Identification Worksheets
- Public Kiosk Guideline Template
- Resources for the Removal of Commonwealth Data from Electronic Media
- Risk Treatment Plan Template
- Scan Treatment Plan Template
- SEC530 Control Summaries
- SEC530 SSP Template - All Controls
- SEC530 SSP Template - Organization Controls
- SEC530 SSP Template - Non-Sensitive System Controls
- SEC530 SSP Template - Sensitive System Controls
- Security Roles and Responsibilities Template
- System Inventory and Definition Template
- VDEM Continuity Plan Template
- VDEM Guide to Identifying Mission Essential Functions
- Vulnerability Scanning and Intrusion Detection System (IDS) Reporting FAQs
- Commonwealth Project Management Guideline (CPM 110-05) (Word version)
- Project Management Standard (CPM112)
- Project Manager Selection and Training Standard (CPM 111)
Visit Project Management Division (PMD) for more information.
- Technology Management Policy (GOV105-05)
- Information Technology Investment Management (ITIM) Standard (CPM-516)
Visit IT Investment Management for more information.
